Based on published source code and conversations with the woman behind the Parler dump (donk_enby on Twitter), I can completely explain how the Parler data was acquired, and why it was legal. The story making the rounds on Reddit claiming that she somehow hacked Parler and got admin access is third-hand bad techno-madlibs fiction. What she actually did was reverse-engineer the protocol (API) used by the Parler iOS app to communicate with the website backend.
 Sean Whalen
Sean Whalen
Ohio’s absentee ballot system disenfranchises disabled voters. Let’s fix that before November.
I was born with cerebral palsy — neurological damage from a lack of oxygen to the brain at birth. Each person with this condition is affected differently, and to varying degrees. Some may have balance issues; others may have mental impairments. For me and many others, cerebral palsy causes muscle spasticity. In my case, my muscles are so tight that my range of motion is very limited. Practically, the biggest impacts for me are not being able to walk without assistance, drive, or write legibly at all.
Despite these challenges, I have a high-paying, stable job in information security for one of the largest medical and pharmaceutical distributors in the world. I am acutely aware of two things: how critical our role is in ensuring that hospitals get the supplies they need during the COVID-19 pandemic, and how privileged I am to still be working during a time when most businesses have been required to close, leading to historic levels of unemployment.
I have lived in Ohio all my life. I have voted in person for nearly every election since I turned 18. The COVID-19 pandemic has changed lives around the world, and has caused many states to conduct voting almost entirely by mail, including Ohio. I have found that Ohio’s process for absentee voting is needlessly difficult or impossible for voters like me. Ohio’s Secretary of State has made exceptions so that people with disabilities are permitted to vote in person at their local county Board of Elections on voting day. However, they risk catching or spreading the virus that way. Some changes are needed to make Ohio’s elections better for everyone, regardless of ability or party affiliation.
How to forward a forensic copy of an email as an attachment
If you receive a fraudulent email, can be very useful to send a full forensic copy to an organization that is being spoofed, industry partners, and law enforcement.
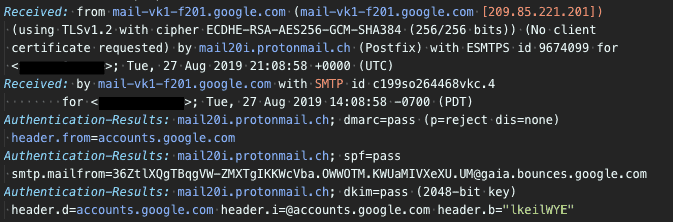
When a user clicks forward in a mail client, the client copies the message’s content and attachments to a new message. The original message headers are not included.
In order to send a full forensic sample that includes the original message headers, the original message must be sent as an attachment in a new message. The process for doing this varies by mail client.
How to view email headers
Email headers contain very useful information for tracing a message’s origin and troubleshooting its delivery. Email headers are written with the oldest headers at the bottom, and the newest headers at the top. By reading the headers in the correct order, you can see how the message was passed from one mail server to another, and the actions each mail server took along the way.
Most email clients have a function to display a message’s headers. The exact steps depends on the client.
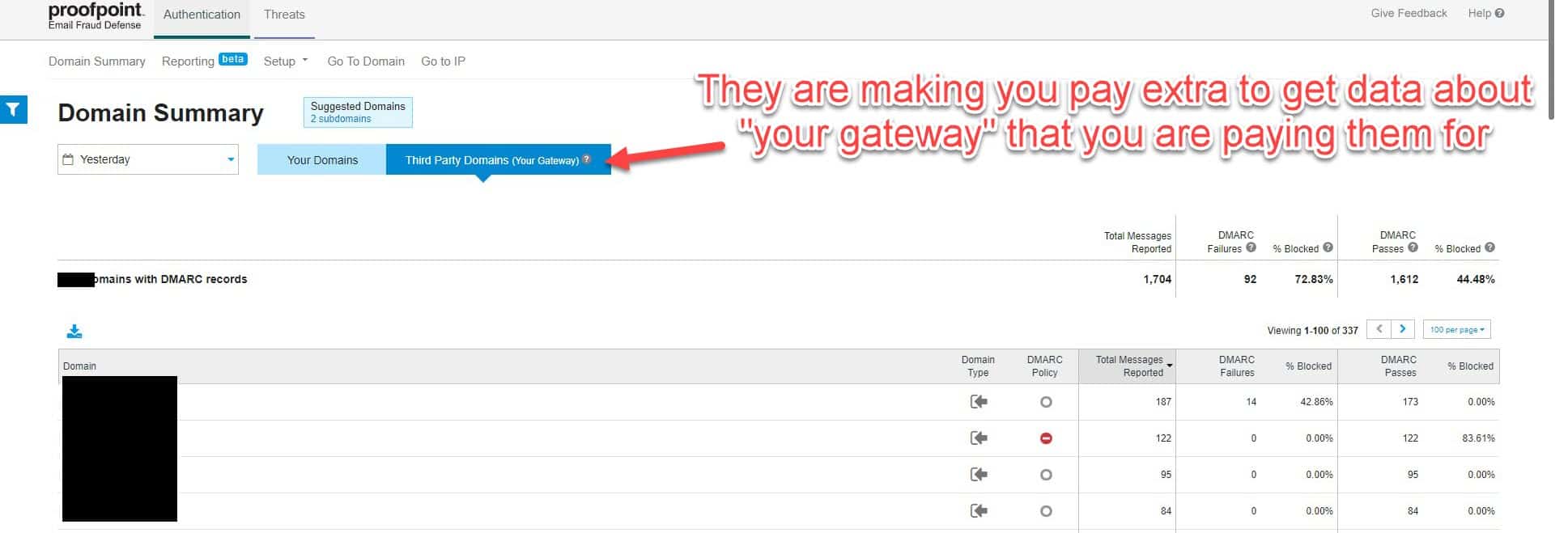
Proofpoint is requiring their customers to pay for Email Fraud Defense to get aggregate DMARC data from their gateways
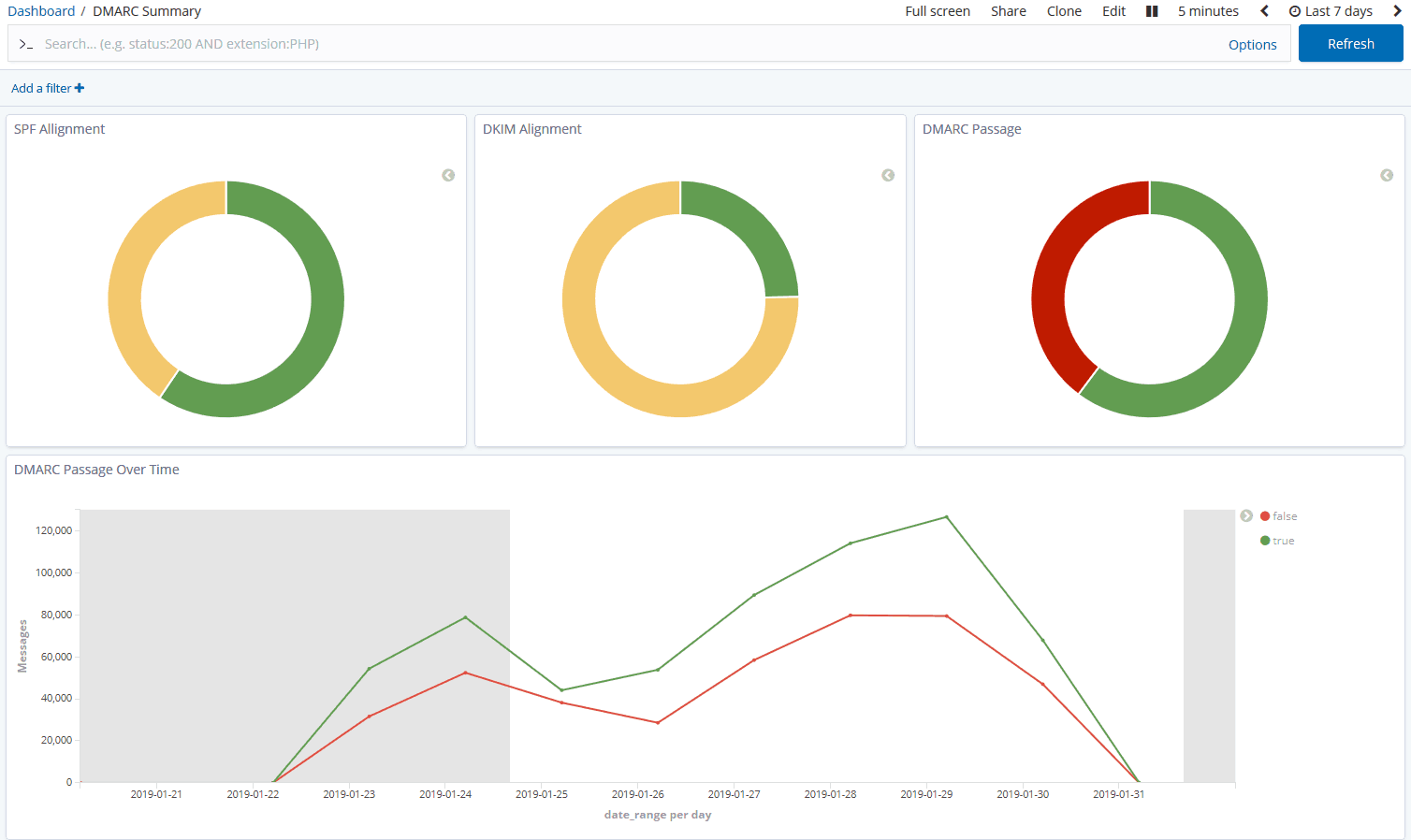
I have written extensively about the DMARC email security standard, including publishing a comprehensive guide on how to implement it, with or without additional third-party vendors. I also do a little consulting on DMARC deployment best practices. One of those consulting clients uses Proofpoint for their email gateway. They also use Dmarcian, a reasonably priced DMARC report analytics service that also publishes a ton of public content for the good of the community. We were considering moving the client’s DMARC policy from monitor only (p=none) to an enforced state (p=reject) after many hours of steadily improving the SPF and DKIM alignment of their email sources. As I took another look at the aggregate (rua) DMARC data in Dmarcian, I noticed something odd: Dmarcian was getting aggregate reports from all of the expected third-party email recipients, like Google, Yahoo, Comcast, and the client’s industry partners, but I didn’t see any reporting from the client’s own Proofpoint Secure Email Gateway (SEG).
Emotet malspam campaign exploits reliance on magic for file type detection
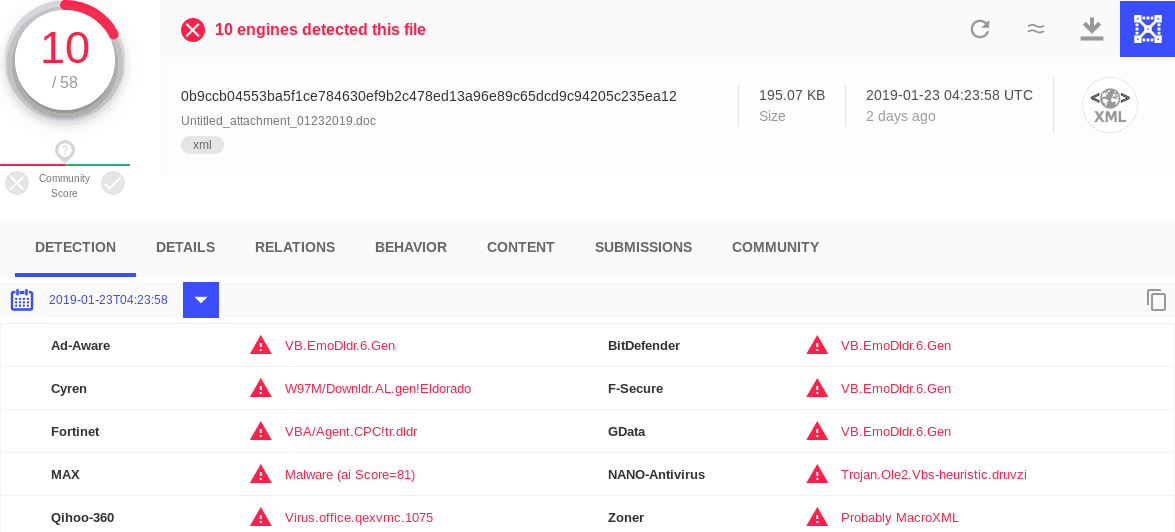
Emotet is a Trojan designed to steal banking information. It is frequently spread by sending phishing emails to governments, banks, healthcare organizations, and schools. The phishing emails will often claim to be an invoice, with a malicious Microsoft Word document attached. The email may often appear to be from a trusted supplier. Once the attachment or link is opened, the target is prompted to click “Enable content”, which would allow the dropper to install Emotet.
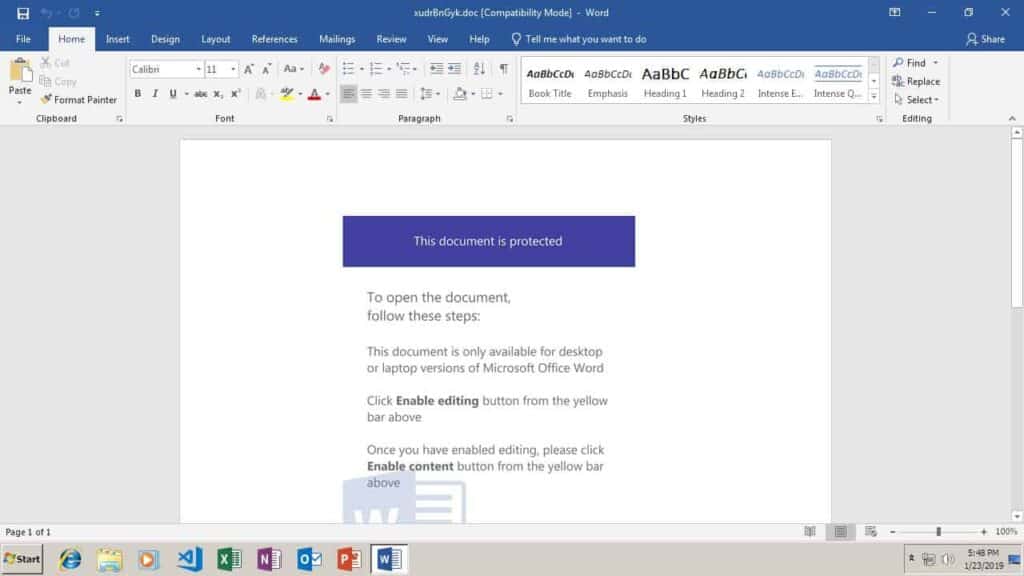
I recently encountered two Emotet dropper samples (0b9ccb04553ba5f1ce784630ef9b2c478ed13a96e89c65dcd9c94205c235ea12 and eff6619aee017ee5d04c539ff12c63a199a1e489660f7156b95e562667393d3c) that would not run correctly in my malware sandbox. I soon found the cause of the problem: the file type had been detected as a generic XML file, rather than what it really is: a Microsoft Word document.
How to inspect the certificate of a mail server over a CLI
If you ever need to inspect the certificate of a remote SMTP server, you can use the openssl CLI tool.
If you need to check STARTTLS:
openssl s_client -connect mail.example.com:25 -starttls smtp
Or, for a standard secure SMTP port:
openssl s_client -connect mail.example.com:465
To save the certificate to a file, just redirect the output:
openssl s_client -connect mail.example.com:25 -starttls smtp > mail.example.com.crt
You can also check SMTP TLS using MX Toolbox or Check TLS.
Demystifying DMARC: A guide to preventing email spoofing
DMARC can stop spoofed spam and phishing from reaching you and your customers, protecting your information security and your brand. However, complexity and misconceptions deter many organizations from ever deploying it. Part mythbusting , part implementation guide, this post explains the shortcomings of SPF and DKIM, what DMARC is, how to deploy DMARC properly, and how to respond to DMARC reports – all without the need for an additional vendor, thanks to open source software!
How to compile and install FFmpeg on Debian/Ubuntu
Here’s how to build and install FFmpeg from source with all the bells and whistles (i.e codec support). We’ll install it as a custom Debian package using checkinstall. That way, any other package that depends on the ffmpeg package will recognize that it is already installed, and won’t try to fetch it from the Debian or Ubuntu software repositories.
Stop the ADA Education and Reform Act
The Americans with Disabilities Act (ADA) of 1990 (amended in 2008) is a bipartisan law that sets accessibility standards that businesses open to the public must follow, so that those with disabilities can work, shop, dine, and play just like any other citizens. Title III of the ADA requires basic necessities like ramps, handicap parking spaces, and doorways wide enough for a wheelchair. Even under current law, the accommodations must not place an “undue burden” on the business, and be “readily achievable“. In other words, the accommodations must be practical and affordable. As a result of 27 years of building access equality, these features have become so ubiquitous that it’s easy for anyone to take them for granted. However, the enforcement mechanism that has been in place for nearly three decades is now in jeopardy because of H.R.620 – The ADA Education and Reform Act of 2017, sponsored by Rep. Poe, Ted [R-TX-2].