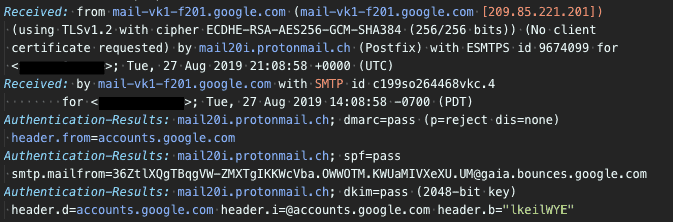
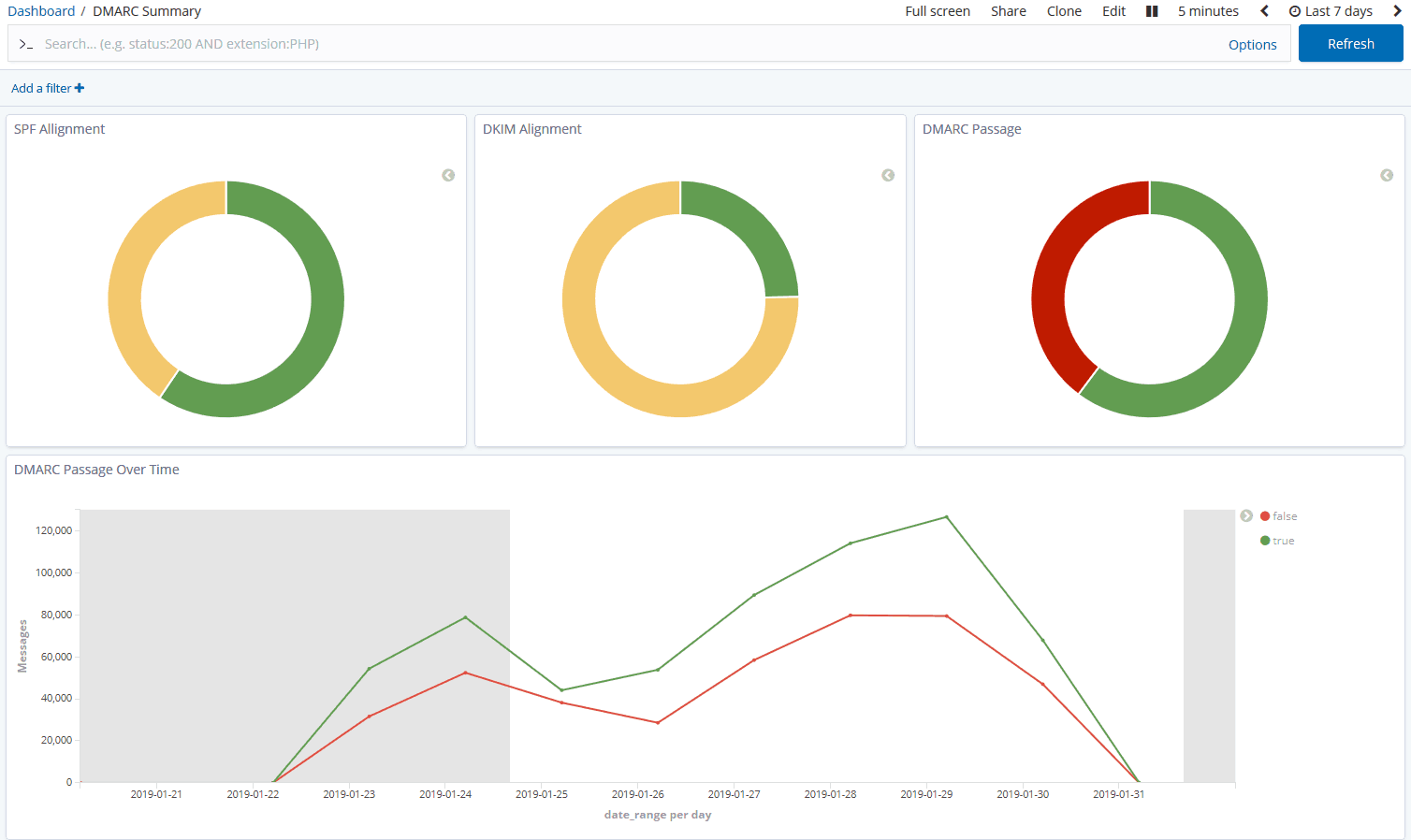
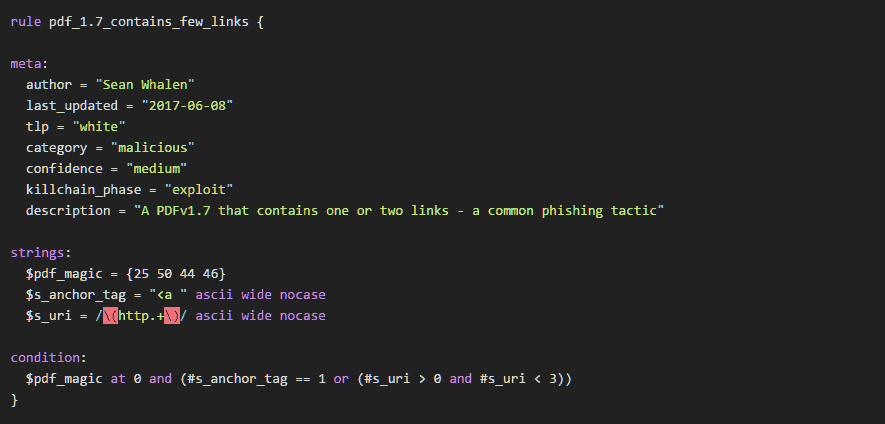
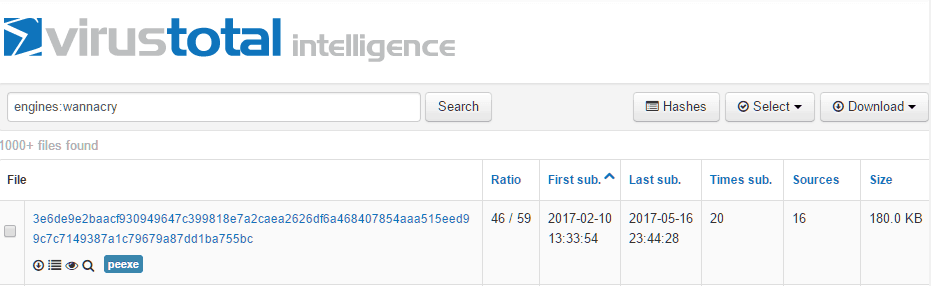
Email headers contain very useful information for tracing a message’s origin and troubleshooting its delivery. Email headers are written with the oldest headers at the bottom, and the newest headers at the top. By reading the headers in the correct order, you can see how the message was passed from one mail server to another, and the actions each mail server took along the way.
Most email clients have a function to display a message’s headers. The exact steps depends on the client.