
Ghidra setup guide
A complete setup guide to Ghidra, including perquisites, scripts, and extensions.

A complete setup guide to Ghidra, including perquisites, scripts, and extensions.

This guide covers the basics of building your own malware analysis lab

There are plenty of free resources for malware research, but they should be used with caution

Adding a Keybase proof to a Jekyll site is easy once you know how to do it
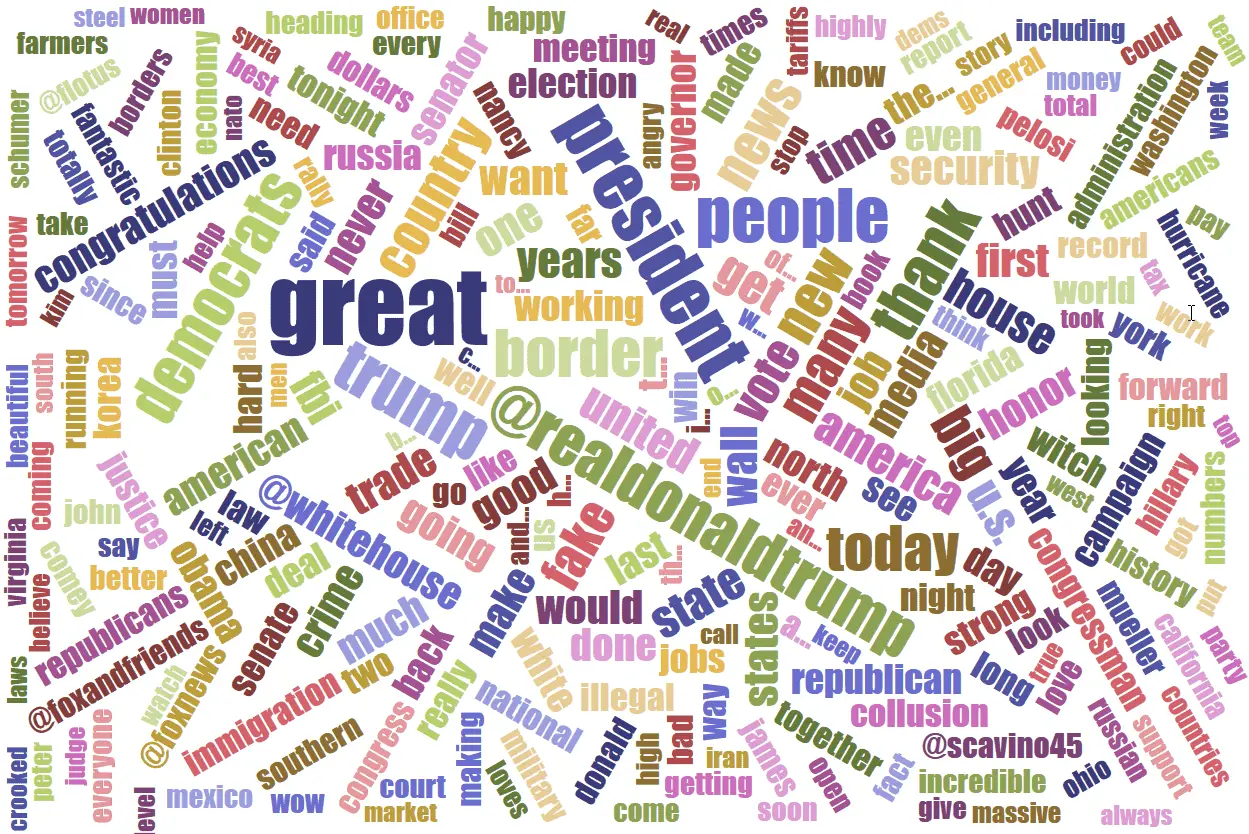
I created a word cloud from nearly a year Donald Trump's tweets in 2019, then forgot to blog about it. Here are the results with a five year retrospective.

Download your media, convert your content to Markdown, and keep your SEO optimizations with one Python script

A journey from a bloated dynamic blog to a svelte static blog

Starting February 2024 Google and Yahoo will start enforcing additional requirements for emails to reach the inbox. Here's how to comply.
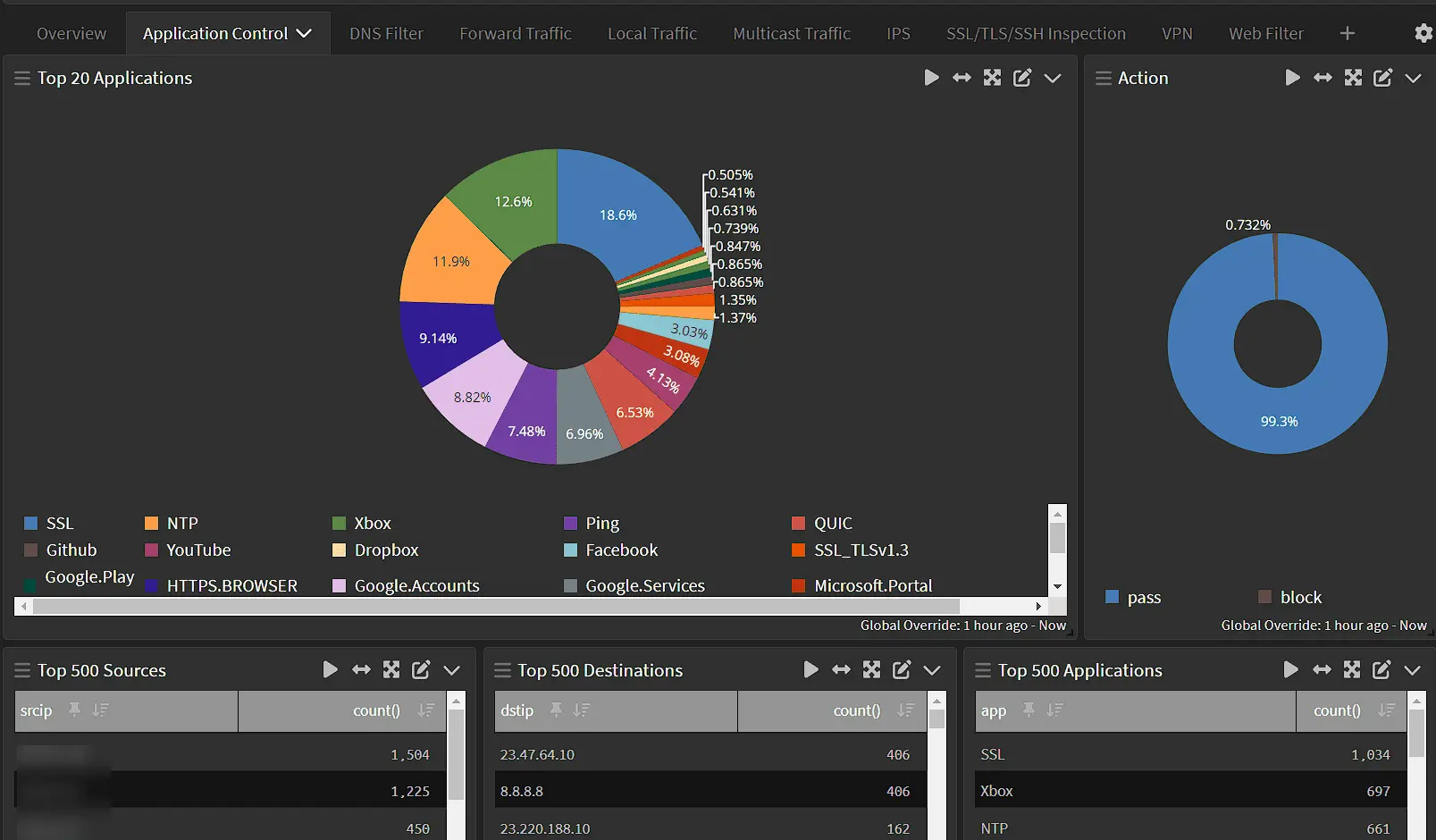
A complete guide to creating a single-node Graylog instance, sending FortiGate firewall logs to it, and analyzing the data

A practical guide to preventing Business Email Compromise by using defense-in-depth techniques, multi-factor authentication, and training