
Why Elon Musk can't buy Bluesky
Developers, data nerds, and VCs have made something special that even Elon Musk can't buy

Developers, data nerds, and VCs have made something special that even Elon Musk can't buy

The domain verification method on Bluesky is simple and transparent – but it comes with some major drawbacks

Your Jekyll site can be used to verify your identify on Bluesky or other platforms that use the AT Protocol
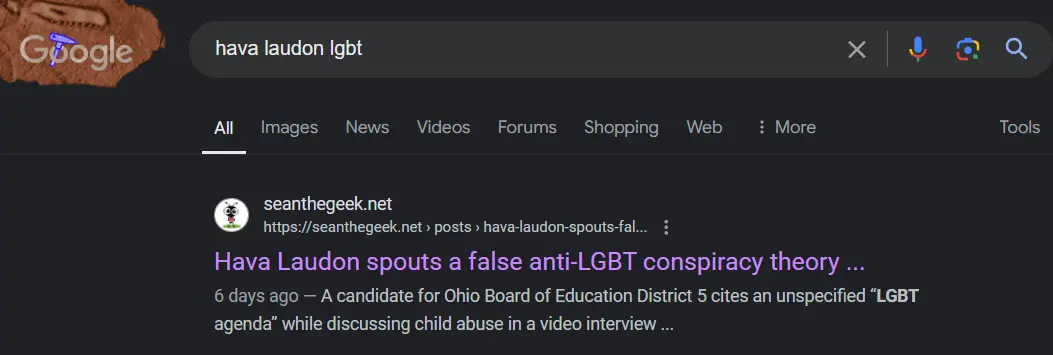
How to rank high in search results without a Big Tech conspiracy

A candidate for Ohio Board of Education District 5 cites an unspecified "LGBT agenda" while discussing child abuse in a video interview posted to her campaign website

My workflow when using Ghidra, plus tips to fix common issues.
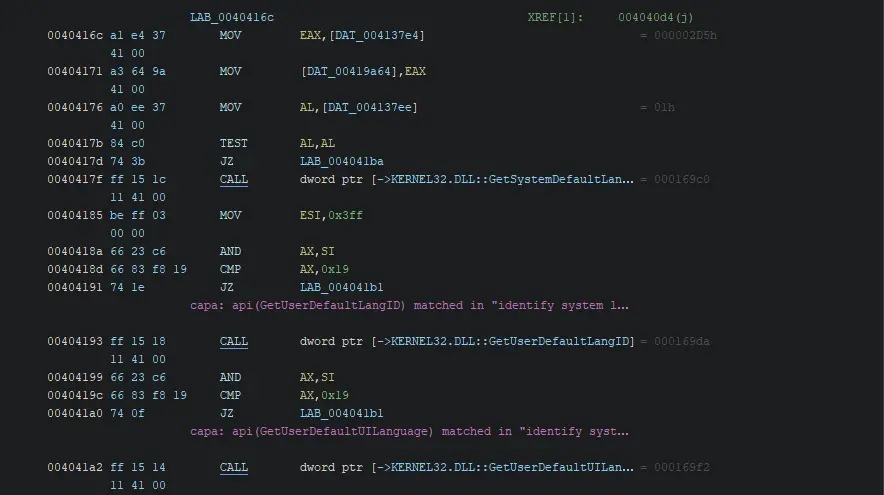
Learn the basics of x86 assembly code for use in dissemblers like Ghidra, IDA, and Binary Ninja, and debuggers like x64dbg.

A guide to the basics of malware analysis and reverse engineering.

A complete setup guide to Ghidra, including perquisites, scripts, and extensions.

This guide covers the basics of building your own malware analysis lab